User's Guide
Content
1. Basic description 2. Background information 3. Installation guide 3.1 Requirements 3.2 Windows installation 4. Usage 4.1 Setting up proxy server and recording protocol traces 4.2 Building a Finite State Automaton 4.3 Constructing Generic Messages Sequences 4.4 Specifying fuzzing functions 4.5 Automating a communication node 4.6 Fuzzing 1. Basic Description AutoFuzz is an open-source framework which provides core functionality to automatically understand network protocol and test/fuzz it for implementation flaws. The framework is divided into two main parts: protocol specification's extraction and fuzzing. Protocol specification's extraction is the approach to understand the network protocol by constructing its Finite State Automaton (FSA) and extracting individual message syntax information from samples of network traces. Traces can be imported externally or recorded using built-in proxy server. The FSA is used to guide the fuzzer through the communication process between two nodes and to keep an overall "picture" of the fuzzing progress. The fuzzer stores individual message syntax information in Generic Message Sequences (GMSs). GMSs are constructed using using algorithms of bioinformatics such as global and local alignment. GMS separates static data fields from dynamic values where each dynamic value has an associated type information. The FSA together with the GMSs can be used to improve the quality of the test cases, and reduce the run-time of overall testing. The framework allows adding support to "learn" new protocols, as well as to extend the existing fuzzing functions. 2. Background information * AutoFuzz fuzzes protocol implementation by modifying traffic between the communication nodes. To do that, AutoFuzz has a built-in SOCKS v5 proxy server. The proxy server is based on Java Socks Server, but has been modified to allow recording and editing of the traffic. Currently, AutoFuzz supports only plain-text protocols. * AutoFuzz framework allows users to specify which fuzzing functions to use from the available set. One can also add new fuzzing functions (Refer to the Developer's Guide for more details). * In order for AutoFuzz to fuzz all transitions and perform all chosen fuzzing functions, it needs a lot of traffic from the client side (assuming the server side is being fuzzed). Although it is not always necessary to automate a communication node (See section 4.5), it is a common practice. For example, consider a case where one chooses to fuzz a server node of the SMTP communication. In this case, the author's preferred method would be to write a small automated smtp client in python. See section 4.5 for other suggestions or '[MainDrive]:\[ProgramFiles]\AutoFuzz\Samples\smtpPythonClient.py' for an example, if you have AutoFuzz installed.* A successful fuzzing is identified by application's unepected behaviour in forms of the system or the application crash, unexpected output or state change. Once the unexpected behavoir occurs you will able to trace the sequence of transitions taken by the fuzzer as well as the fuzzed message from the fuzzing log files. Please refer to [MainDrive]:\[ProgramFiles]\AutoFuzz\Logs\ 3. Installation Guide 3.1 Requirements * JRE 1.6+ * Jung graph framework jar file 3.2 Windows Installation * Right click on WindowsIntallAutoFuzz.bat and select "run as administrator" * Add the jung *.jar to the java classpath * Right click on "[MainDrive]:\[ProgramFiles]\AutoFuzz\AutoFuzz.jar" and "run as administrator" 4. Usage 4.1 Setting up proxy server and recording protocol traces 1. Specify a proxy port and click on "Start proxy". Make sure to allow inbound traffic on the firewall on the port specified. 2. Click on "Start Recording Traffic" to start a new protocol trace. 3. Once sufficient traffic has been recorded click "Stop Recording Traffic". Collect as many protocol traces as you think is sufficient in order to cover the protocol functionality that will be tested. 4. You can save the traffic that is recorded by clicking "Export App. Traffic" or re-import it later by clicking "Load App. Traffic".
4.2 Building a Finite State Automaton 1. Choose the abstraction function. 2. Click "Construct FSM". 3. Click "Minimize FSM" to minimize the FSA and to restore loops from the protocol traces (Note, that loops are not included in the original representation of the FSM). 4. Verify that the FSA has been successfully minimized by viewing "Minimized FSA".
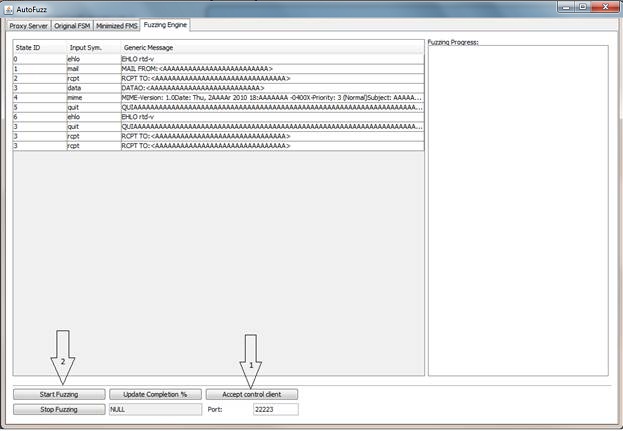
4.3 Constructing Generic Message Sequences (GMS) 1. To generate GMSs click on "Init. Fuzzing Engine". 2. Once the process is complete you can view the resulting GMSs under "Fuzzing Engine" tab. (Note, that a considerable amount of algorithms is involved in constructing GMSs. Therefore, initialization might take anywhere from a few minutes to half-hour or more).
4.4 Specifying fuzzing functions 1. Please refer to [MainDrive]:\[ProgramFiles]\AutoFuzz\fuzzingFunctions.txt 4.5 Automating a communication node If needed, it is possible to automate one of the communication nodes using various techniques: 1. Write an automated node using standard python or other libraries (see [MainDrive]:\[ProgramFiles]\AutoFuzz\Samples). 2. Replay previously recorded traffic. 3. Forward real traffic from a life network. 4.6 Fuzzing 1. First, open up a Command and Control Socket so that the automated node can reset the fuzzing state. Confirm that the firewall is not block incoming connections on it. 2. Click on "Start Fuzzing" (Make sure the proxy server is running).